Employee PII: A Major Risk for Critical Utility Infrastructure
The landscape of national security has shifted. In 2026, the frontline of defense for critical infrastructure—power grids, water treatment facilities, and telecommunications—is no longer just the perimeter of the corporate firewall; it is the personal privacy of the employees who operate them.
Cybercriminals and nation-state threat actors have moved beyond simple brute-force attacks. Instead, they are increasingly leveraging Personally Identifiable Information (PII) scraped or purchased from data brokers to launch sophisticated, human-centric attacks. For critical infrastructure providers, the exposure of an employee’s home address, personal phone number, or family details is a direct vulnerability to the industrial control systems (ICS) they manage.
1. The Human Vulnerability in Critical Infrastructure
Critical infrastructure (CI) sectors, such as water and energy, are uniquely targeted because their disruption has immediate, cascading effects on public safety and the economy. In 2025 and 2026, reports from agencies like the CISA Water and Wastewater Systems Sector Toolkit and private firms like Cyble have noted a massive spike in "Initial Access" operations targeting the individuals who hold the keys to Operational Technology (OT).
The Role of PII in Modern Attacks
Threat actors use PII to bridge the gap between an employee’s private life and their professional access. When a hacker knows where an engineer lives, who their spouse is, and what their personal cell phone number is, they can craft attacks that are indistinguishable from legitimate interactions.
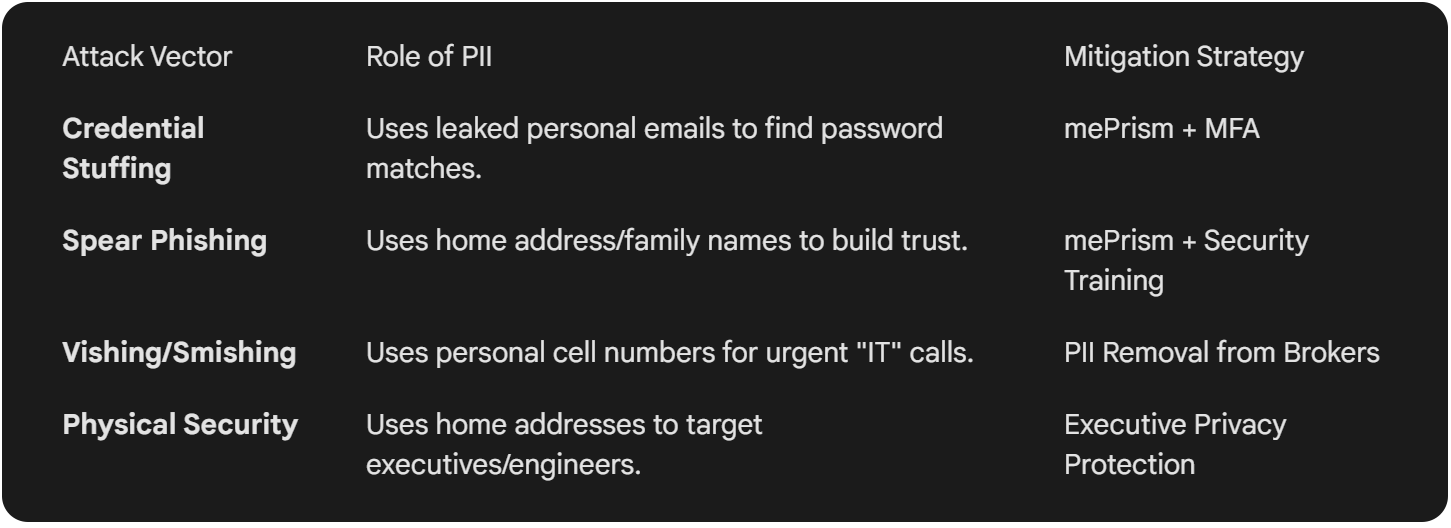
Common attack vectors powered by employee PII include:
Hyper-Personalized Spear Phishing: Using family names or recent life events to trick employees into clicking malicious links.
Vishing (Voice Phishing): Using personal phone numbers to call employees, often impersonating IT staff or executives, to harvest credentials.
Physical Coercion and Doxing: Threatening to release an employee’s private data or targeting their home network to gain a foothold into the corporate VPN.
2. Data Brokers: The Arsenal for Cyber Criminals
Cybercriminals rarely "hack" their way to an employee's personal data; they buy it. Data brokers—companies that aggregate and sell personal data—have become the "arms dealers" of the digital age.
Recent Consumer Financial Protection Bureau (CFPB) rulemaking has highlighted the need to stop these brokers from selling sensitive data to scammers and foreign spies.
How Data is Scraped and Sold
Data brokers collect billions of data points from public records, social media, retail loyalty programs, and mobile app permissions. This data is then compiled into comprehensive "person profiles" that include:
Full names and aliases.
Current and past home addresses.
Personal email addresses and cell phone numbers.
Social Security Numbers (SSNs) and birth dates.
Relative and neighbor information.
Property records and financial estimates.
For a few dollars, a threat actor can purchase a list of every control room operator at a specific regional water utility. This "reconnaissance-as-a-service" allows attackers to bypass the traditional reconnaissance phase of the Cyber Kill Chain, moving directly to exploitation.
Note: Research from NATO’s Strategic Communications Centre of Excellence highlights that the lack of regulation in the data broker industry makes it a "gold mine" for foreign intelligence services and criminal syndicates looking to map out the personnel of sensitive facilities.
Is your data being used against you?
We scan hundreds of data broker sites to see exactly where your home address, phone number, and family details are exposed. It takes 60 seconds to see what they know about you.
Because your data shouldn’t be a roadmap for violence.
3. Threat Vectors: From Data Points to Power Outages
The transition from a leaked home address to a compromised power grid follows a predictable path.
Stage 1: Identification: The attacker identifies a target organization, such as a municipal water district. They use LinkedIn or company websites to find employees with high-level access (e.g., SCADA engineers, IT directors).
Stage 2: Profile Building: The attacker queries data brokers or "People Search" sites (like Whitepages, Spokeo, or MyLife) to obtain the personal contact information of these individuals.
Stage 3: The "Life-Hack" Phish: Armed with personal details, the attacker sends a message to the employee’s personal email or SMS. Because it mentions the employee's real address or a family member, the employee is significantly more likely to trust the sender.
Example: An SMS alert seemingly from the employee’s actual home security provider, asking them to "log in" to check a false alarm. The login page is a credential harvester designed to capture the employee's master password.
Stage 4: Lateral Movement to OT: Once the personal credentials are stolen, the attacker tests them against the company's VPN or remote access portals. If the employee reuses passwords—a common occurrence—the attacker gains access to the internal network. From there, they can move laterally to the Operational Technology (OT) network that controls physical machinery, such as water pumps or circuit breakers.
4. Why mePrism Privacy is Now "Best Practice"
Historically, cybersecurity was focused on "inside the building." However, the Department of Energy and CISA now emphasize a "Shields Up" mentality that includes protecting the digital footprint of the workforce, as detailed in the CISA Strategic Roadmap for Secure and Resilient Water Sector.
What is mePrism Privacy?
mePrism Privacy is a specialized service that automates the removal of PII from over 600 data broker and "people search" websites. For critical infrastructure companies, deploying a service like mePrism is no longer just a "perk" for employees; it is a critical security control.
How mePrism Hardens the Perimeter
Continuous Scanning: mePrism uses AI-driven bots to constantly scan the web for an employee’s data.
Automated Opt-Outs: Instead of an employee spending hundreds of hours manually submitting "opt-out" requests to shady brokers, mePrism handles the legal and technical process of data removal.
Monitoring for Re-listing: Data brokers often "re-scrape" data. mePrism provides 24/7 monitoring to ensure that once data is removed, it stays removed.
5. The Business Case for PII Protection in Utilities
Utility companies are increasingly adopting mePrism for several strategic reasons:
A. Reducing the "Initial Access" Surface According to the Palo Alto Networks (Unit 42) 2025 Incident Response Report, social engineering remains the #1 initial access vector. By removing the data that makes these attacks possible, companies drastically reduce the probability of a successful breach.
B. Liability and Duty of Care When an employee is doxed or targeted at home because of their role at a utility company, the organization faces significant legal and reputational liability. Providing a privacy protection service demonstrates a "Duty of Care" for the workforce, which can lower insurance premiums and improve employee retention.
C. Regulatory Compliance New EPA guidelines for cybersecurity in the water sector regarding water system security highlight the need for "hygiene" that extends to remote access and credential management. Removing PII is a foundational step in preventing the unauthorized remote access that these agencies are trying to curb.
6. The 2026 Threat Landscape: Geopolitical Tensions
The urgency of PII protection is underscored by current geopolitical tensions. State-sponsored actors have been documented "pre-positioning" themselves in U.S. critical infrastructure, a threat discussed in depth by Lawfare regarding the national security problem of data brokerage.
Research from late 2025 showed that "Initial Access Brokers" (IABs) are increasingly selling access to utility networks on the dark web. These IABs use scraped PII to find the "path of least resistance" into a company—often a single, unprotected employee.
7. Implementation: A New Standard for CISOs
For the modern CISO of a water or power company, the "Human Risk Management" strategy must now include Digital Privacy Protection.
Inventory: Identify "High-Value Targets" (HVTs) within the organization—those with administrative or OT access.
Deployment: Enroll these employees in a service like mePrism Privacy.
Education: Teach employees why their personal data is a corporate risk. When employees understand that their home address is a backdoor into the city's water supply, they are more likely to participate in privacy programs.
Conclusion
The weaponization of PII has changed the rules of engagement for critical infrastructure. In an era where data brokers sell the blueprints of an employee’s life for pennies, the "castle and moat" strategy of cybersecurity is obsolete.
By proactively removing employee data from the ecosystem via services like mePrism Privacy, critical infrastructure providers can "blind" their attackers. This shift from reactive defense to proactive privacy protection is not just a trend; it is the new best practice for any organization responsible for the essential services that keep society functioning.
Protecting the grid now begins with protecting the people who run it.
Ready to try mePrism yourself?
If you're a company protecting at-risk employees, or an individual concerned about your digital footprint, start your privacy removal today at mePrism.com.
Because your data shouldn’t be a roadmap for violence.
Explore more from Our Team
Browse more posts written by our team to help you stay in control.
Be Part of the Conversation